ClickFix: How to Infect Your PC in Three Easy Steps – Krebs on Security
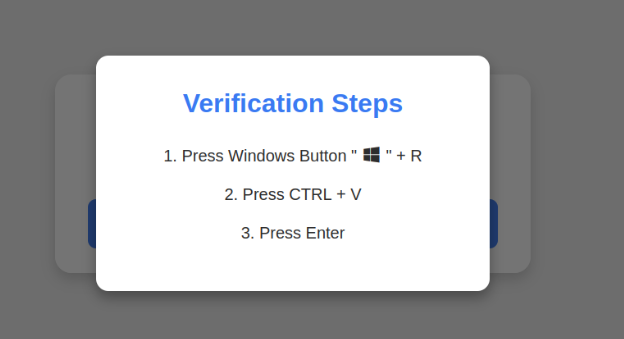
A clever malware deployment scheme first spotted in targeted attacks last year has now gone mainstream. In this scam, dubbed “ClickFix,” the visitor to a hacked or malicious website is asked to distinguish themselves from bots by pressing a combination of keyboard keys that causes Microsoft Windows to download password-stealing malware.ClickFix attacks mimic the “Verify You are a Human” tests that many websites use to separate real visitors from content-scraping bots. This particular scam usually starts with a website popup that looks something like this:This malware attack pretends to be a CAPTCHA intended to separate humans from bots.Clicking the “I’m not a robot” button generates a pop-up message asking the user to take three sequential steps to prove their humanity.Executing this series of keypresses prompts Windows to download password-stealing malware.Step 1 involves simultaneously pressing the keyboard key with the Windows icon and the letter “R,” which opens a Windows “Run” prompt that will execute any specified program that is already installed on the system.Step 2 asks the user to press the “CTRL” key and the letter “V” at the same time, which pastes malicious code from the site’s virtual clipboard.Step 3 — pressing the “Enter” key — causes Windows to download and launch malicious code through “mshta.exe,” a Windows program designed to run Microsoft HTML application files.“This campaign delivers multiple families of commodity malware, including XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT,” Microsoft wrote in a blog post on Thursday. “Depending on the specific payload, the specific code launched through mshta.exe varies. Some samples have downloaded PowerShell, JavaScript, and portable executable (PE) content.”According to Microsoft, hospitality workers are being tricked into downloading credential-stealing malware by cybercriminals impersonating Booking.com. The company said attackers have been sending malicious emails impersonating Booking.com, often referencing negative guest reviews, requests from prospective guests, or online promotion opportunities — all in a bid to convince people to step through one of these ClickFix attacks.In November 2024, KrebsOnSecurity reported that hundreds of hotels that use booking.com had been subject to targeted phishing attacks. Some of those lures worked, and allowed thieves to gain control over booking.com accounts. From there, they sent out phishing messages asking for financial information from people who’d just booked travel through the company’s app.Earlier this month, the security firm Arctic Wolf warned about ClickFix attacks targeting people working in the healthcare sector. The company said those attacks leveraged malicious code stitched into the widely used physical therapy video site HEP2go that redirected visitors to a ClickFix prompt.An alert (PDF) released in October 2024 by the U.S. Department of Health and Human Services warned that the ClickFix attack can take many forms, including fake Google Chrome error pages and popups that spoof Facebook.ClickFix tactic used by malicious websites impersonating Google Chrome, Facebook, PDFSimpli, and reCAPTCHA. Source: Sekoia.The ClickFix attack — and its reliance on mshta.exe — is reminiscent of phishing techniques employed for years that hid exploits inside Microsoft Office macros. Malicious macros became such a common malware threat that Microsoft was forced to start blocking macros by default in Office documents that try to download content from the web.Alas, the email security vendor Proofpoint has documented plenty of ClickFix attacks via phishing emails that include HTML attachments spoofing Microsoft Office files. When opened, the attachment displays an image of Microsoft Word document with a pop-up error message directing users to click the “Solution” or “How to Fix” button.HTML files containing ClickFix instructions. Examples for attachments named “Report_” (on the left) and “scan_doc_” (on the right). Image: Proofpoint.Organizations that wish to do so can take advantage of Microsoft Group Policy restrictions to prevent Windows from executing the “run” command when users hit the Windows key and the “R” key simultaneously.
This entry was posted on Friday 14th of March 2025 06:15 PM
I know every change breaks someone’s workflow, but I don’t see any compelling reason why the Run menu needs to accept pasted text.Oooh boy you would break my life if you removed paste from Run. I live in the Run window. Sometimes I use it to very quickly and efficiently remove formatting from copied text (win+r -> ctrl+v-> ctrl+a -> ctrl+x -> esc). Sometimes i use it to open copied links quickly (they open in the default browser). Sometimes I use it to compose an email to a copied email address (win+r -> type “mailto:” -> ctrl+v). The list goes on.Ooooh boy you would break my life if you removed paste from Run. I live in the Run window. Sometimes I use it to very quickly and efficiently remove formatting from copied text (win+r -> ctrl+v-> ctrl+a -> ctrl+x -> esc). Sometimes i use it to open copied links quickly (they open in the default browser). Sometimes I use it to compose an email to a copied email address (win+r -> type “mailto:” -> ctrl+v). The list goes on.Encountered this same malware just about a month ago.
It was invoking powershell script on a remote website.More here: https://www.virustotal.com/gui/url/6212e7c9fa1e1a324005b20aa866041480fca97473c3dd1c5622af3781dedcc5?nocache=1Only 10 of 96 security vendors show this as malware. But fairly certain they do not show everything they can detect on VT, not only in the short term but in the medium and long term as bad guys can also screen their latest malware there.“as bad guys can also screen their latest malware there”No, bad/good guys DO NOT screen their malware on VT. They have their own private VT which does not share samples with researchers and others.Thank you Brian, perfect timing. Doing an anti-fraud presentation at a church on Sunday and will provide this info., to include your website.I disable the Windows key, because the damn thing kept interrupting my games.
Also, I make it a rule never to use the browser that came with the operating system. No matter their assurances, it’s bound to get privileges a browser shouldn’t have.if I own a computer I ought to be able to run things on it easily so I want win r. how did websites get access to put things on my clipboard, thus being one step closer to owning my machine?That’s actually what the first button click is for: it’s the required user interaction before a website may write something to your clipboard. But to answer your question:
According to the compatibility table at https://developer.mozilla.org/en-US/docs/Web/API/Clipboard_API, websites have been write text to clipboard on click since 2018.
But IIRC that feature was introduced to mimic identical functionality in Adobe Flash Player, so the real answer is: a really long timeim coming right 4 u – Cheshireserves booking.com right for how they rip off consumersVery use-full. Info like this makes it worth putting up with your politics.I once received an email with some subject line that told me it was from Microsoft and urgent to read and then the message in the email was well written with grownup words and correct grammar. The message in the email told me to “click on this link to fix the problem.” DUH. The link I clicked on instantly downloaded and installed a virus that destroyed the contents of my hard drive. As a computer professional with advanced skills and education, I felt like a moron afterward. I’ll never forget my father shaking his head and repeatedly telling me “You? I cannot believe that someone like you would have done this!” I ended up having to pay a colleague with a better tech background than me to restore my hard drive and operating system.Brian, we believe that an employee was presented with this via a vendor site. it appears the vendor site was modified due to an outdated WordPress plugin/vulnerability. There seems to be a lot of this exploit currently on SMB sites built on WordPress.Your email address will not be published. Required fields are marked *Comment * Name * Email * Website
ΔMailing ListSearch KrebsOnSecurityRecent PostsStory CategoriesWhy So Many Top Hackers Hail from Russia
Source: https://krebsonsecurity.com/2025/03/clickfix-how-to-infect-your-pc-in-three-easy-steps/



