Hijacking AirTag Infrastructure To Track Arbitrary Devices – Hackaday
In case you weren’t aware, Apple devices around you are constantly scanning for AirTags. Now, imagine you’re carrying your laptop around – no WiFi connectivity, but BLE’s on as usual, and there’s a little bit of hostile code running at user privileges, say, a third-party app. Turns out, it’d be possible to make your laptop or phone pretend to be a lost AirTag – making it and you trackable whenever an iPhone is around.The nroottag website isn’t big on details, but the paper ought to detail more; the hack does require a bit of GPU firepower, but nothing too out of the ordinary. The specific vulnerabilities making this possible have been patched in newer iOS and MacOS versions, but it’s still possible to pull off as long as an outdated-firmware Apple device is nearby!Of course, local code execution is often considered a game over, but it’s pretty funny that you can do this while making use of the Apple AirTag infrastructure, relatively unprivileged, and, exfiltrate location data without any data connectivity whatsoever, all as long as an iPhone is nearby. You might also be able to exflitrate other data, for what it’s worth – here’s how you can use AirTag infrastructure to track new letter arrivals in your mailbox!They’re linking the paper from their main site now:
https://cs.gmu.edu/~zeng/papers/2025-security-nrootgag.pdfThe gist seems to be that, on systems where you have local execution but can’t change the MAC address, you can still make AirTag-style BLE broadcasts with that MAC address, even though AirTags are supposed to have an Apple OUI.
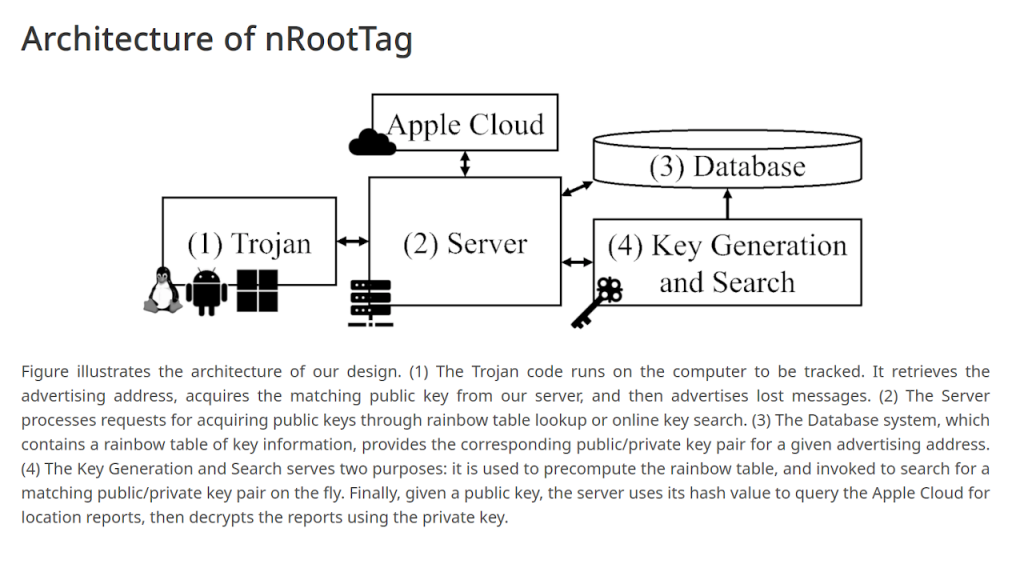
Then they use a GPU cluster to find a collision between their broadcast address and a legitimate-looking one with an Apple MAC. Pretty nifty.This is just as doable with Google’s FindMy network, actually much easier. No need for a fancy GPU cluster to vanitysearch the used elliptic curve, just set the right eddystone BLE advertisement on your compromised system. I really love hacking on those network for years now, and this use case is indeed very troubling.Same deal with Amazon Sidewalk network, which uses ring cameras and echo assistants.This is why Apple and Android have stalking protection out of the box..In their paper, the trojan is actually connecting to a server to acquire the required pre-computed key to be broadcast (the bidirectional connection between 1 and 2 in the diagram). It isn’t clear to me why this is done on the server vs the client: is calculating these keys is just an computational impossibility on the client, or the table of keys too large to store in the trojan itself? Or just a PoC, so just showing one particular implementation to demonstrate it is possible?In any case, it is ingenious, but I don’t see any practical or nefarious use as illustrated – it is just easier to get the trojan app to share the target’s location with the server in the first step and skip FindMy!The trojan sends the target’s MAC address, and the server which has access to a lot of compute will calculate a compatible public key to be broadcasted (the MAC address on Apple’s FindMy is part of the public key bytes). It’s really basic vanitysearch, as done with crypto coin addresses to have the start of the public address something you choose beforehand.I need sending a message like meshtasticPlease be kind and respectful to help make the comments section excellent. (Comment Policy)This site uses Akismet to reduce spam. Learn how your comment data is processed.
By using our website and services, you expressly agree to the placement of our performance, functionality and advertising cookies. Learn more
Source: https://hackaday.com/2025/03/03/hijacking-airtag-infrastructure-to-track-arbitrary-devices/